Authentication vs Authorization
If you are struggling with the concept of authentication and authorization, well here is kinda good news. These two concepts are not as hard as you are thinking but really important to build any kind of software application. After reading this post, you will have a solid understanding of these two "seems like confusing concepts".
What are they?
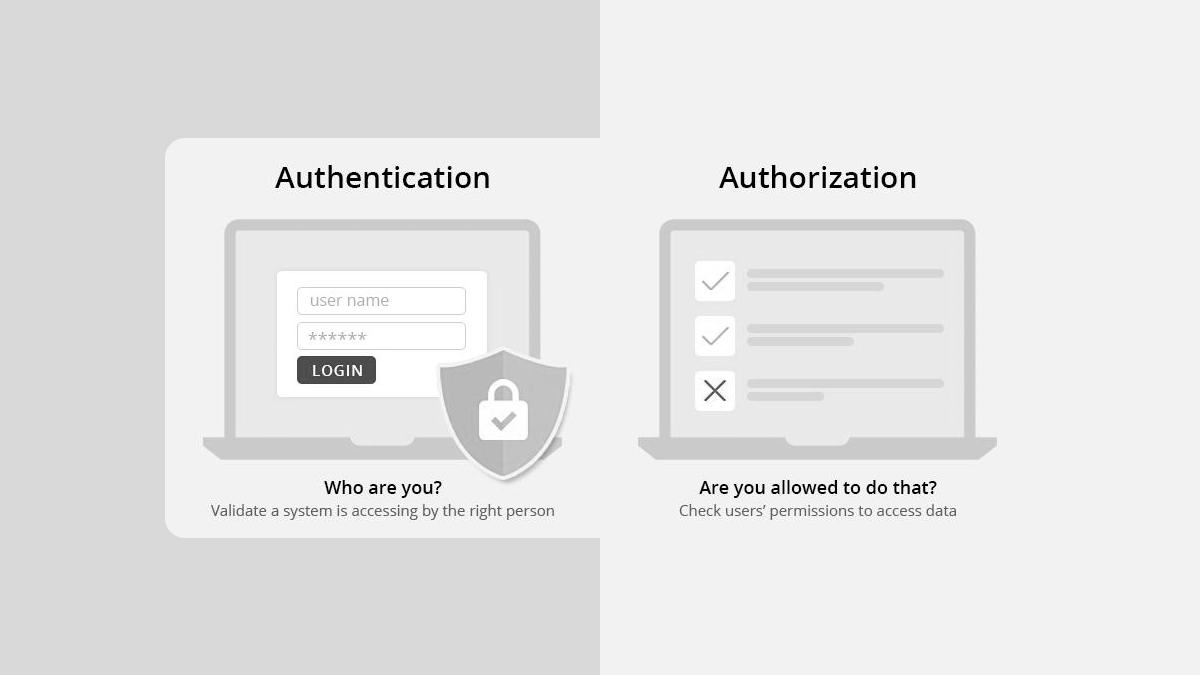
Authentication is the process of verifying the identity of a user, device, or system. It involves verifying that the entity claiming to be who they say they are actually is who they claim to be.
Authorization is the process of granting or denying access to resources or actions based on the identity of the user, device, or system. It involves deciding whether an authenticated entity has the necessary permissions to perform a specific action or access a particular resource.
Here are some examples.
- Online banking: When you log into your online banking account, you are required to enter your username and password. This is the authentication step, as it verifies your identity. Once you are authenticated, you are then able to perform certain actions, such as transferring money or viewing your account balance. This is the authorization step, as it determines what you are allowed to do based on your authenticated identity.
- Accessing a secure building: When you enter a secure building, you may be required to present a badge or swipe a card to gain entry. This is the authentication step, as it verifies that you are an authorized employee or visitor. Once you are authenticated, you may only be allowed to access certain areas of the building based on your role or clearance level. This is the authorization step, as it grants or denies access to specific areas based on your authenticated identity.
- Using a smartphone app: When you download and open a smartphone app, you may be required to log in with your username and password. This is the authentication step, as it verifies your identity. Once you are authenticated, the app may grant you access to certain features or functions based on your permissions. For example, a productivity app may allow you to create and edit documents, but not delete them, based on your authorization level.
Now that you understand the basics, let's advance further.
What are the available technologies?
You might be wondering which technologies are typically used to achieve this in a web application. Well, there are several technologies that can be used.
For authentication:
- Single Sign-On (SSO) systems: SSO systems allow users to log in to multiple web applications using a single set of credentials, such as a username and password. This can make it easier for users to access multiple applications without having to remember multiple sets of login information. SSO systems are often used in enterprise environments, where users may need to access a large number of internal applications.
- OAuth: OAuth is an open standard for authorization that allows users to grant third-party applications access to their resources without sharing their login credentials. OAuth is commonly used for social media login integrations, where users can log in to a web application using their Facebook or Google accounts.
- JSON Web Tokens (JWTs): JWTs are a popular method for authenticating and authorizing users in web applications. They are digitally signed tokens that contain information about the user and their permissions. JWTs can be easily passed between servers and clients, making them useful for API authentication and authorization.
- Cookies: Cookies are small pieces of data that are stored on the user's device and sent back to the server with each request. They can be used to store information about the user's session, such as their authenticated identity and permissions.
- HTTP Basic and Digest Authentication: HTTP Basic and Digest Authentication are methods for authenticating users using the HTTP protocol. They involve sending the user's login credentials with each request, either in the header or as part of the URL.
- Biometric authentication: Biometric authentication involves using unique physical characteristics, such as a fingerprint or facial recognition, to verify the identity of a user. This type of authentication is becoming more common on smartphones and other devices.
- Multi-Factor Authentication (MFA): MFA involves using more than one method to verify the identity of a user. This can include something the user knows (such as a password), something the user has (such as a phone or security token), or something the user is (such as a fingerprint). MFA provides an additional layer of security by requiring multiple pieces of evidence to verify the user's identity.
And for authorizations:
- Role-Based Access Control (RBAC): RBAC is a method of granting or denying access to resources based on the user's role or job function. Users are assigned to specific roles, and each role is given a set of permissions that determine what actions the user is allowed to perform.
- Access Control Lists (ACLs): ACLs are a way of specifying which users or groups are allowed to access specific resources. Each resource is associated with an ACL that lists the users or groups that are allowed to access it, as well as the actions they are allowed to perform.
- OAuth: OAuth is an open standard for authorization that allows users to grant third-party applications access to their resources without sharing their login credentials. OAuth is commonly used for social media login integrations, where users can log in to a web application using their Facebook or Google accounts.
- JSON Web Tokens (JWTs): JWTs are a popular method for authenticating and authorizing users in web applications. They are digitally signed tokens that contain information about the user and their permissions. JWTs can be easily passed between servers and clients, making them useful for API authentication and authorization.
- Cookies: Cookies are small pieces of data that are stored on the user's device and sent back to the server with each request. They can be used to store information about the user's session, such as their authenticated identity and permissions.
- HTTP Basic and Digest Authentication: HTTP Basic and Digest Authentication are methods for authenticating users using the HTTP protocol. They involve sending the user's login credentials with each request, either in the header or as part of the URL.
So, what is the usual flow of authentication and authorization?
The authentication and authorization flow of a web application typically involves the following steps:
- The user attempts to access a protected resource or perform a restricted action on the web application.
- The web application prompts the user to enter their login credentials, such as a username and password.
- The user enters their credentials and submits them to the web application.
- The web application verifies the user's credentials against a stored set of valid credentials. This is the authentication step.
- If the user's credentials are valid, the web application grants the user access to the protected resource or allows them to perform the restricted action. This is the authorization step.
- If the user's credentials are not valid, the web application denies access and may prompt the user to try again or provide an error message.
Depending on the specific technology being used for authentication and authorization, the details of this process may vary. For example, if the web application is using OAuth for authentication, the user may be redirected to a login page hosted by a third-party provider (such as Google or Facebook) to enter their credentials. If the web application is using JWTs for authorization, the user may be issued a token upon successful authentication that contains information about their permissions and is passed with each subsequent request to the web application.
What is the typical HTTP response?
Here is a description of typical HTTP responses for both authentication and authorization in success and error states:
Authentication success:
- If the user's login credentials are successfully verified, the web application may return an HTTP 200 OK response.
- In some cases, the web application may also return an HTTP 302 Found response, redirecting the user to a protected resource or the home page of the application.
Authentication error:
- If the user's login credentials are invalid or cannot be verified, the web application may return an HTTP 401 Unauthorized response.
- The web application may also include a WWW-Authenticate header in the response, indicating the authentication method being used (such as Basic or Digest) and providing a challenge for the user to retry the authentication process.
Authorization success:
- If the user is successfully authorized to access a protected resource or perform a restricted action, the web application may return an HTTP 200 OK response.
- Depending on the specific resource or action being accessed, the web application may also return other HTTP status codes, such as HTTP 201 Created for resource creation or HTTP 204 No Content for actions that do not return a response body.
Authorization error:
- If the user is not authorized to access a protected resource or perform a restricted action, the web application may return an HTTP 403 Forbidden response.
- The web application may also include a WWW-Authenticate header in the response, indicating the authorization method being used and providing a challenge for the user to retry the authorization process.
In conclusion, if the system asks "Who are you?" to validate the right person, this is authentication. When it checks "Are you allowed to do that?" by checking the user's permission to access the resources, you guessed it right, this is an authorization. If you like this post, please share and subscribe to my blog.
Happy New Year 2023!


Member discussion